If you own a smartphone and regularly use it for web browsing, the chances are that you might feel a little safer than you would while doing so on a desktop or laptop PC. However, this isn’t actually the case, as in many instances mobile sites and apps have similar levels of security vulnerability to ordinary websites. Fake and insecure apps and a lack of encryption are surprisingly common.
Recently, it was revealed that a huge number of fake apps were available for download in the Google Play store, the marketplace for apps for Android smartphones and tablets. Many fakes were replicas of genuine apps available for Android devices, while others were actually crude copies of apps designed purely for iPhones, each of them carrying varying security threat levels.
Pre-Christmas rush
Many of these fake apps were released just before Christmas, coinciding with a time when many people will have received new Android devices as presents, eager to get the latest apps from the very first use. Many of these apps have been designed with malicious intent, containing malware or a means of trying to take money from you such as a payment gateway.
Meanwhile, it has recently been revealed that a large proportion of the top 90 mobile banking apps have at least some security vulnerabilities. Research into some of the biggest mobile apps available from major global, regional and national banks found that there were several ways in which criminals could intercept them, using phishing or other forms of malware to get what they want.
Open to yet more threats
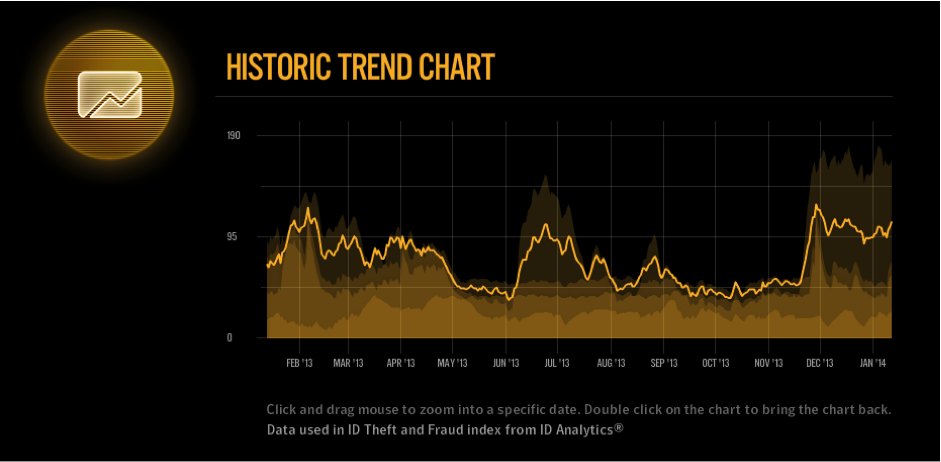
According to Norton’s cybercrime index, there may be a myriad of threats looming for anyone using banking apps in order to manage their money. 90% of top apps have non-SSL links, which means that some transactions made via these apps could be hijacked at any time. Banks from all over the world could be implicated in this mass-ignorance of online security for users of their apps.
To try and help protect their customers, banks are being advised to ensure that all connections are made with a valid SSL certificate, removing all code for the app description on either the App Store or Google Play store and try to ensure that further use is prohibited in the event of infection. Thus far, a small number of banks have responded fully.